Security
We take your trust seriously.
Physical Security
Our offices are monitored by CCTV and have 24-hour security present. They are equipped with alarm systems and armed response. Centralised storage, where used, is within secured areas with access control restricted to named users.
Our primary hosted services reside within Xneelo’s data centres, which are monitored by internal and external CCTV, as well as 24-hour security. Access control is restricted by biometrics and the facility is designed with VESDA (Very Early Smoke Detection Apparatus) installed.
Outside of South Africa, we make use of Amazon Web Services, a Cloud provider spanning 69 availability zones in 22 regions. Security of the AWS cloud is incredibly high including infrastructure security, DDoS protection, Identity and Access Control and Data Encryption.
Encryption
In transit encryption is achieved by Transport Layer Security (TLS), or where applicable, IPSec Tunnels. Where IPSec tunnels are not in place and files are required to be transferred, Secure FTP is instituted.
Authentication and Passwords
Some of our offerings include Single Sign-On, which is achieved by means of OAuth. This allows you as the client to sign in using familiar and standardised credentials.
Password complexity is configurable to your requirements, including the following:
- Password expiration
- Password reset link expiration
- Welcome link expiration
- Minimum password length
- Requirements for Uppercase, Lowercase, Numbers, and Symbols
- Custom Allowable Symbols
Secure password generation is also available within Eyerys.
Scheduled Penetration Testing
Penetration tests are regularly executed against our environment, with remediation efforts on any findings addressed as first priority. We use reputable external security providers for these exercises to obtain a balanced and unbiased view of the environment in order to provide the best security to you. More information around our testing is available to clients upon request.
Access Control
Logical access to our servers for maintenance is strictly controlled internally and is limited to named, authenticated users. Privileged accounts are more strictly controlled than regular accounts.
Solutions hosted within our online platform are logically segregated, preventing cross-site scripting and privilege escalation between accounts and tenants.
From an application point of view, our clients are given full rights to manage their own access control within the system. As such, it is the responsibility of the customer to ensure that their access control to the system is managed according to good practice.
Our datacentres and hosting locations are outsourced to industry leaders, who maintain strict control and security of the environments. Security controls include physical access control, logical access control, and Intrusion Prevention systems.
Baseline Configurations
Our servers are all configured to stringent baseline configuration standards. If we provision a new service, you can rest assured that it has security pre-applied to it and does not rely on insecure defaults in configuration.
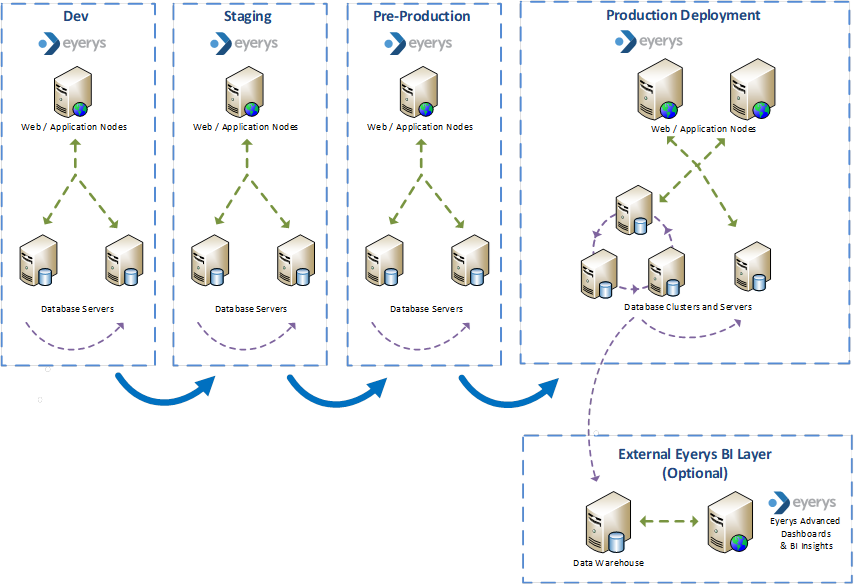
Topology
Database servers and clusters are segregated securely from web and application servers to ensure edge security. Development, Staging and Pre-Production environments, where applicable, are segregated entirely from Production deployments.
Intrusion Prevention
Our physical offices are secured by alarm systems, 24/7 access control and CCTV systems. While we do not host your services at our administrative offices, we maintain strict control over who has access to our internal systems. All systems are access controlled and are inaccessible to non-employees or outside of designated team members. Centralised storage is located within our secured cloud or within a secure server room with strict, named access control.
Our hosted servers are protected by industry-standard intrusion prevention systems and include other security measures such as DDoS mitigation, VLAN protection and strict firewall rules.